SSH Hardening — Case Study (In Progress)
Will document threat model, configuration changes, validation steps, and operational trade-offs for an exposed SSH service.
Focused on SSH and NGINX configuration review, exposure reduction, and operational safety for Linux systems.
Contact for scope discussion:
I work with individuals and small teams operating Linux servers who need to reduce exposure risk, harden default configurations, or validate existing SSH and NGINX setups.
Typical environments include VPS instances, cloud VMs, and small on-prem systems that are internet-facing.
Review and hardening of OpenSSH configurations including authentication methods, cipher selection, access controls, and logging with attention to common attack patterns.
Configuration review for TLS, headers, request handling, and information exposure, including documentation of trade-offs and compatibility considerations.
User permissions, firewall rules, service exposure, and logging review for Linux servers.
These offerings focus on configuration review and risk reduction. They are not penetration tests or compliance certifications.
I work primarily with Linux servers and exposed services, focusing on configuration review, hardening, and operational safety. This site documents my approach, configurations, and case-study-driven work rather than marketing claims.
Contact
Documented examples and in-progress case studies.
Will document threat model, configuration changes, validation steps, and operational trade-offs for an exposed SSH service.
Will include TLS configuration, header hardening, request handling, and before/after comparisons.
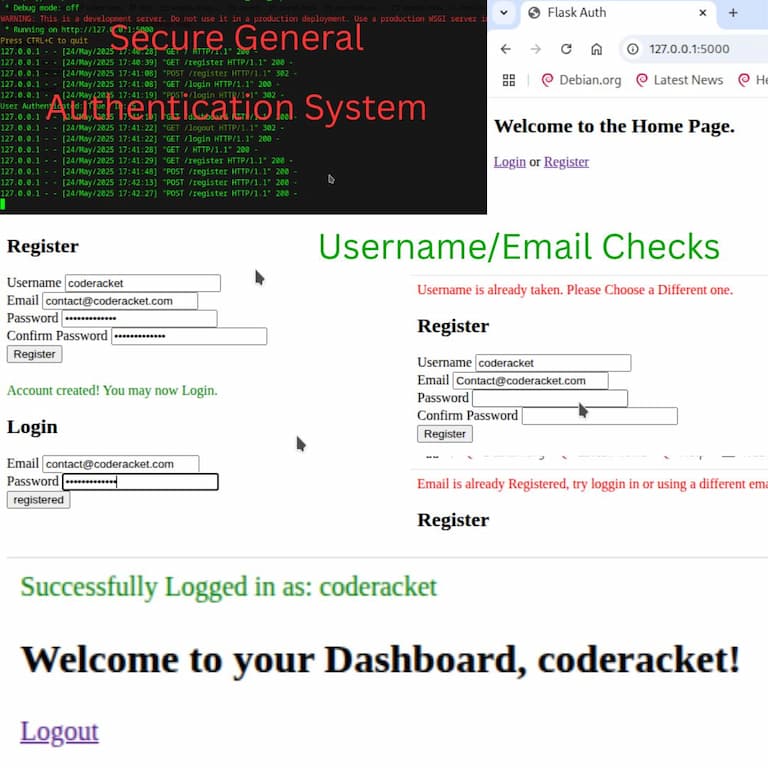
Demonstrates application-layer secure defaults. Included for context only and not a primary service offering.
View CodeFor scope discussion or questions regarding an existing Linux server or service configuration.